Compliance and legal readiness are critical in highly regulated industries like healthcare, finance, and education. However, managing vast amounts of email data can complicate retention and deletion decisions.
Data archiving addresses this challenge by securely centralizing email records, ensuring compliance, and simplifying access for audits and ediscovery. A key feature that supports these processes is the audit trail — a detailed, immutable log of all actions on archived emails.
This article will explore:
- What is an audit trail and why it’s important
- The challenges of data retention, archiving, and ediscovery
- How emails can become evidence
- How role-based permissions can help
What Is an Audit Trail and Why Is It Important?
An email archiving solution needs to guarantee a tamper-proof archive in order for the business to stay compliant and ediscovery-ready.
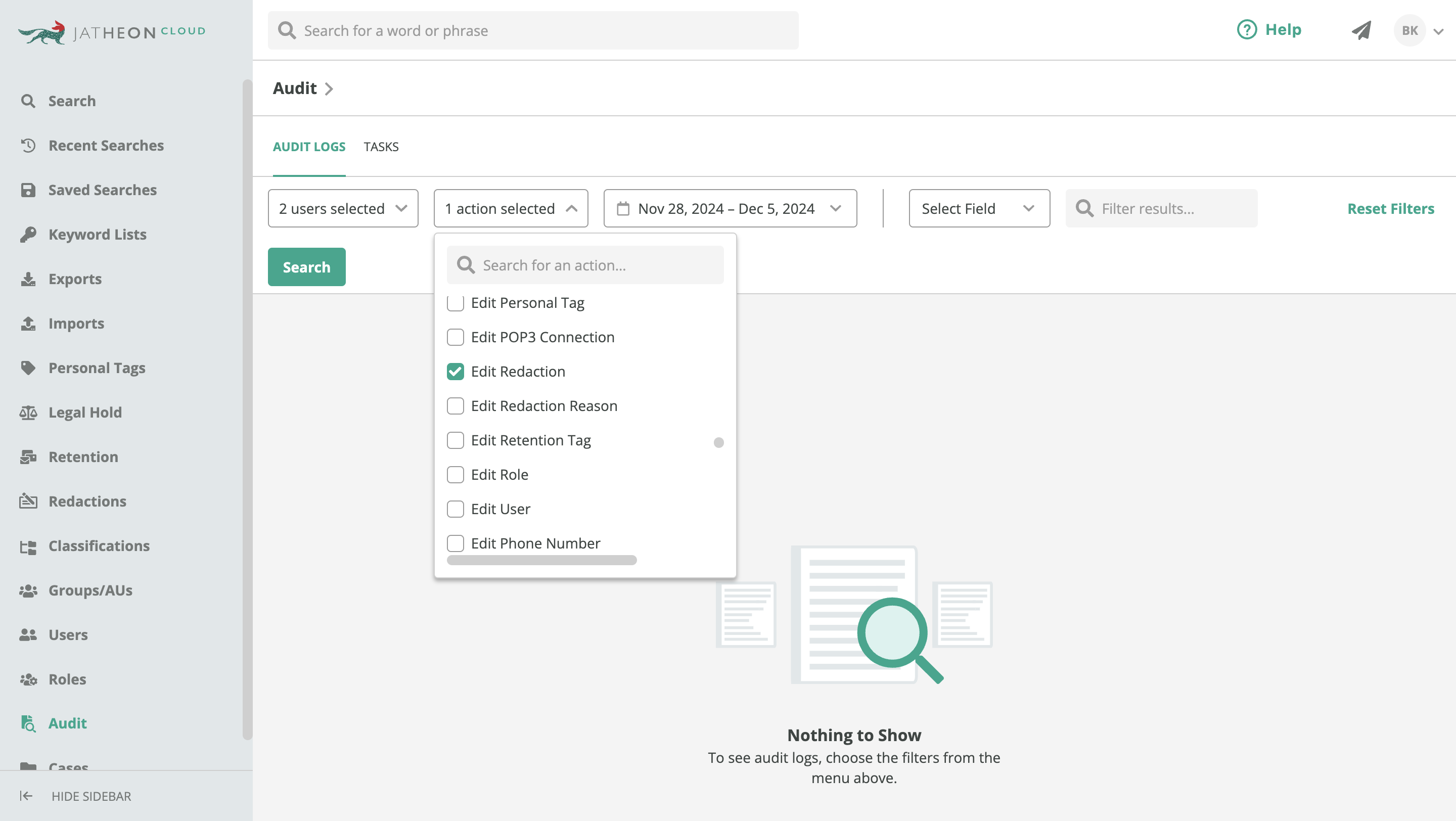
An audit trail is a detailed, chronological record of all actions taken within a system. In the context of email archiving, it tracks activities such as:
- Who accessed specific emails
- What actions were performed (e.g., view, export, delete)
- When each action occurred
One of the biggest advantages of email archiving is that it prevents the deliberate or inadvertent manipulation of your important files. This is vital because the company needs to prove the integrity of specific emails in case they’re used as evidence in a legal case.
Email archiving solutions allow admins and compliance officers to perform audits.
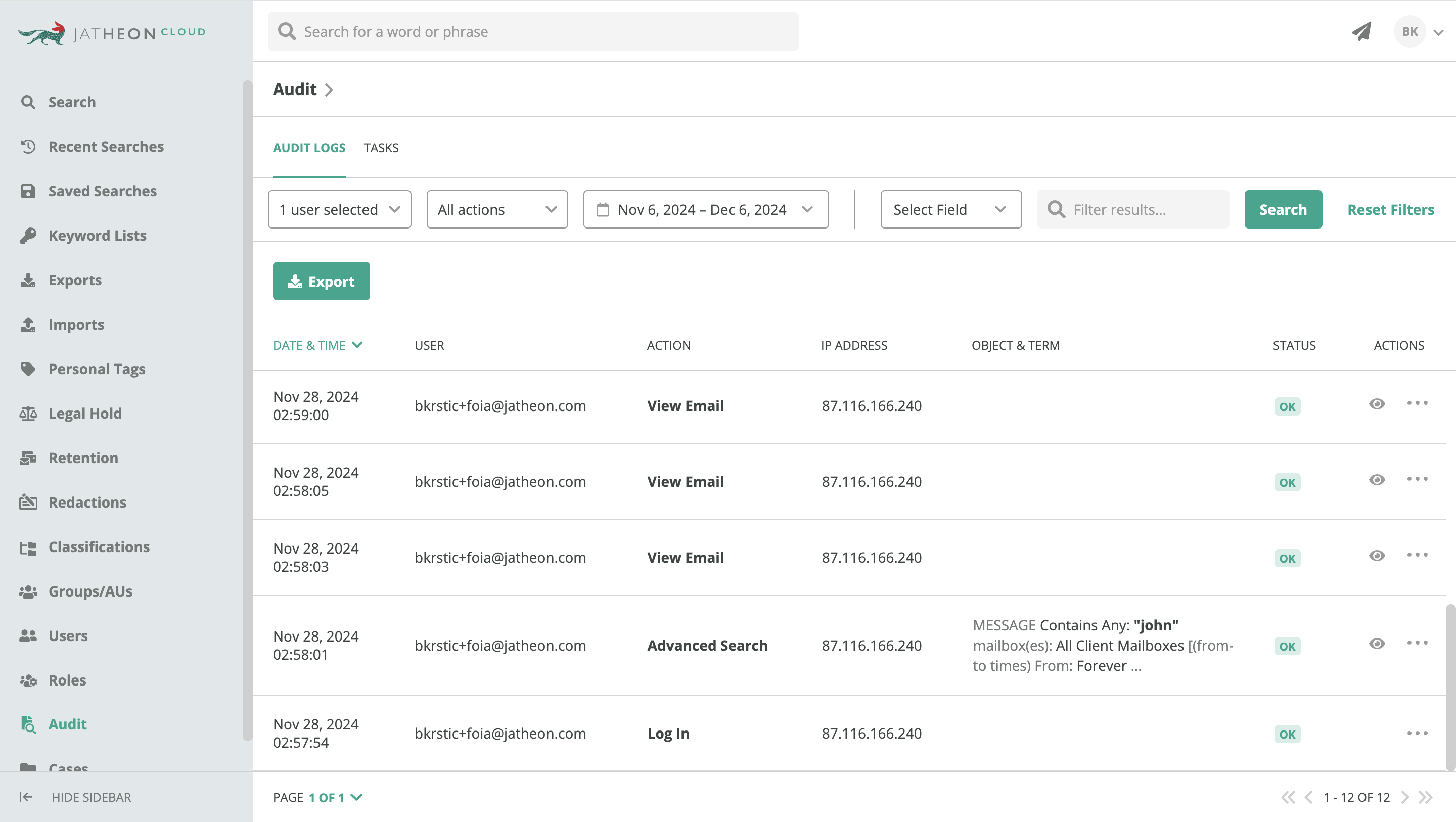
The audit trail feature offers a read-only log which is used to track activities on the archiving software. It also allows authorized staff members to view the history of activities of a specific user (or another compliance officer) within a specific date range.
For instance, if an employee attempts to access a section they are not authorized to access, this activity will be recorded in the audit log.
The software allows admins to check whether specific keywords have been searched, which users looked for what data, whether they attempted to modify certain rules, or whether somebody tried to overstep their authority.
To remain compliant with industry laws and regulations, you have to make sure your archiving solution offers full audit trails. Monitoring user activities will give you the ultimate control of your data, allow you to track unauthorized activities or attempts at viewing other people’s data, prevent data alterations and ensure full regulatory compliance.
An audit trail example would be a healthcare provider facing an HIPAA investigation. Regulators request proof that only authorized personnel accessed a patient’s protected health information (PHI.) With audit trail software, the organization can quickly produce a log showing:
- Which users accessed the relevant emails
- The exact time and date of access
- Any subsequent actions, such as forwarding or exporting
This detailed record satisfies HIPAA audit trail requirements, ensuring compliance and avoiding penalties.
Key Benefits of Audit Trails
- Tamper prevention — Audit trails protect archived data from unauthorized manipulation, whether intentional or accidental. By maintaining a secure, unalterable record of actions, you can ensure the authenticity of sensitive information and uphold compliance with regulations.
- Enhanced oversight — Administrators and compliance officers rely on audit trails to monitor system activity by tracking who accessed what data and when, organizations can quickly detect and address unauthorized actions or potential security breaches. This oversight helps reduce compliance risks and maintain a secure system.
- Proof for legal cases — Detailed audit logs provide clear evidence of proper data handling and retention. When facing audits, litigation, or regulatory investigations, organizations can use these logs to demonstrate compliance and defend against accusations of improper data management.
This level of transparency satisfies regulatory requirements and protects the organization from potential fines and reputational damage. For this reason, audit trails act as a critical line of defense, ensuring compliance and building trust with regulatory bodies.
The Connection Between Audit Trails and Other Ediscovery Features
Audit trails don’t work in isolation. They complement other ediscovery and compliance features, such as:
- Advanced Search — Ediscovery tools often include advanced search capabilities, allowing users to quickly locate emails based on keywords, senders, recipients, and date ranges. Audit trails record who performed each search, ensuring compliance with data access policies.
- Legal Hold — Legal hold prevents specific data from being altered or deleted during litigation. Audit trails track the implementation of legal holds, providing proof that the organization followed the required procedures.
- Retention Policies — Retention policies automate email deletion after a specified period, reducing storage costs and minimizing risks. Audit trails log any changes to these policies, ensuring transparency.
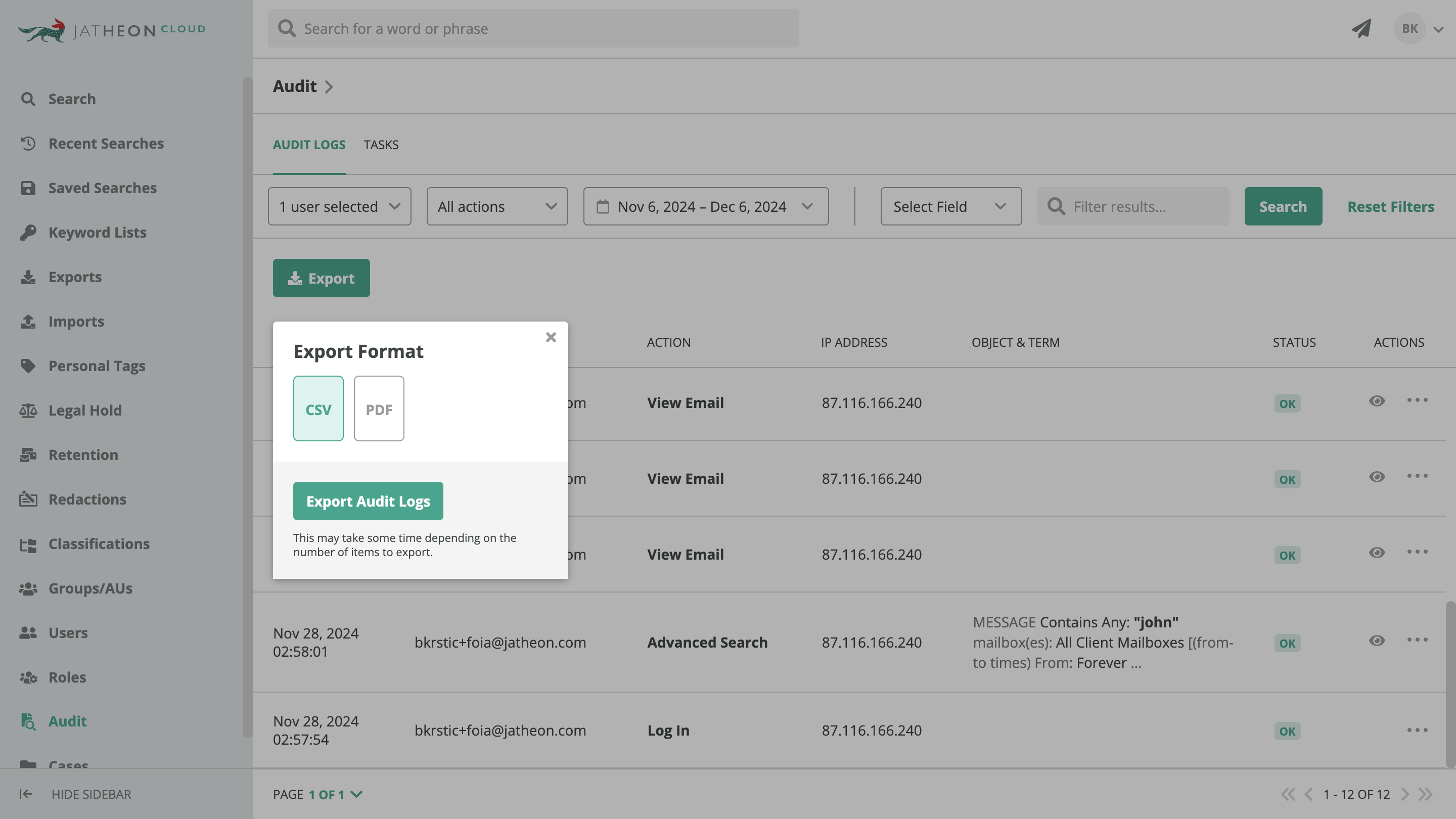
- Export and Reporting — During ediscovery, exporting data is often necessary. Audit trails document every export action, recording who exported the data, when, and for what purpose.
It’s also important to be able to export the actual audit logs in order to present evidence in an acceptable format.
The Role of Audit Trails in Compliance
Regulated industries operate under strict guidelines to protect sensitive data and ensure accountability.
Audit trails are a vital component of compliance strategies, as they provide detailed logs that demonstrate adherence to these regulations. Let’s explore how audit trails help meet specific requirements across key industries:
HIPAA
In the healthcare sector, safeguarding protected health information (PHI) is a legal obligation under HIPAA.
Audit trails provide clear records showing who accessed PHI-related emails and when, to ensure that only authorized personnel interact with sensitive data. This accountability helps prevent unauthorized access, supports internal investigations, and meets HIPAA’s logging and monitoring requirements.
FINRA
Financial institutions regulated by FINRA must maintain accurate, tamper-proof records of communications for audit purposes.
Audit trails document every interaction with archived emails, from searches and views to exports, ensuring that no alterations or deletions occur without detection. This transparency is crucial during financial audits or when responding to regulatory inquiries.
FERPA
For educational institutions, protecting the privacy of student records is essential under FERPA. Audit trails track who accessed emails containing student data, providing an unbroken log of activity to demonstrate compliance with privacy standards.
This is particularly valuable when investigating potential breaches or responding to parental or regulatory inquiries about data handling.
Example in finance
During a FINRA audit, regulators request a detailed history of email communications related to a specific financial transaction. Using an audit trail, the financial institution can generate a report that includes:
- User access logs — Identifying who accessed or searched for the emails in question.
- Export or forward actions — Documenting if any emails were exported or shared externally, including timestamps and recipient details.
- Tamper-proof records — Demonstrating that the emails remained unaltered throughout their retention period
- Retention compliance — Showing the exact duration for which the emails were stored to meet regulatory requirements.
This provides clear evidence of compliance, avoiding potential fines and reputational damage.
Actionable Steps to Implement Audit Trails
- Choose the right archiving solution — Look for software that includes robust audit trail functionality, ensuring it logs all critical activities while maintaining immutability.
- Establish role-based permissions — Define roles and access levels for all users. Audit trail visibility should be restricted to custom roles such as compliance managers or administrators. Regular users should not have access to logs that detail the activities of others, maintaining data privacy and security.
- Regularly review audit logs — Schedule periodic audits of the logs to identify unusual activity, ensure compliance, and address potential risks before they escalate.
- Integrate with compliance tools — Ensure your audit trail integrates seamlessly with other ediscovery and compliance features to create a cohesive system that simplifies regulatory reporting and investigations.
- Train your team — Educate staff on the importance of audit trails, emphasizing the need for accuracy and security. Provide specific training for administrators and compliance personnel on how to monitor and utilize the audit trail system effectively.
Summary of the Main Points
- Audit trails are detailed, time-stamped logs protected from tampering that track all actions within an email archiving system, ensuring compliance, data integrity, and defensibility during audits and litigation.
- They provide accountability by monitoring who accessed emails, what actions were performed, and when, meeting regulatory requirements like HIPAA audit trail mandates.
- Striking a balance is essential—over-retaining data increases costs and risks, while premature deletion may violate compliance rules. Audit trails help ensure data is managed responsibly.
- Since emails can serve as proof of knowledge, provide critical context, or even become conclusive evidence in legal cases, it’s essential to have a robust archiving solution that will ensure immutability and integrity of your email records, preserving them for compliance and legal defensibility.
- Audit trails complement tools like advanced search, legal hold, retention policies, and export capabilities by providing transparency and tracking every interaction to support compliance and litigation needs.
- With audit trails, organizations can meet sector-specific requirements, such as HIPAA for healthcare, FINRA for financial institutions, and FERPA for education. They ensure detailed logs of user actions and safeguard sensitive information.
FAQ
What is the purpose of an audit trail in email archiving?
Audit trails provide a transparent record of actions within the archiving system, helping organizations meet compliance, ensure security, and support legal processes like ediscovery.
Are audit trails mandatory for compliance?
Many regulatory frameworks require organizations to maintain audit trails to demonstrate adherence to data retention and security policies.
How to audit trails enhance security?
They enable organizations to monitor system usage, detect unauthorized activities, and respond promptly to potential threats.
Can audit trails be used for internal investigations?
Yes, audit trails are invaluable for investigating employee misconduct, data breaches, or policy violations.
Can audit trails be tampered with?
No, reputable email archiving solutions ensure that audit trails are immutable and tamper-proof.
How do audit trails support legal holds?
Audit trails track when legal holds are placed, modified, or removed, ensuring transparency during litigation.
Is advanced search connected to audit trails?
Yes, audit trails log all advanced search activities, providing a record of who searched for what data and when.
Read Next:Data Access Governance: A Comprehensive Guide What to Look for in a Cloud Email Archiving Solution |