Metadata is data about data. It gives information about a file, document, or piece of content, like its author, date and time created, or file size.
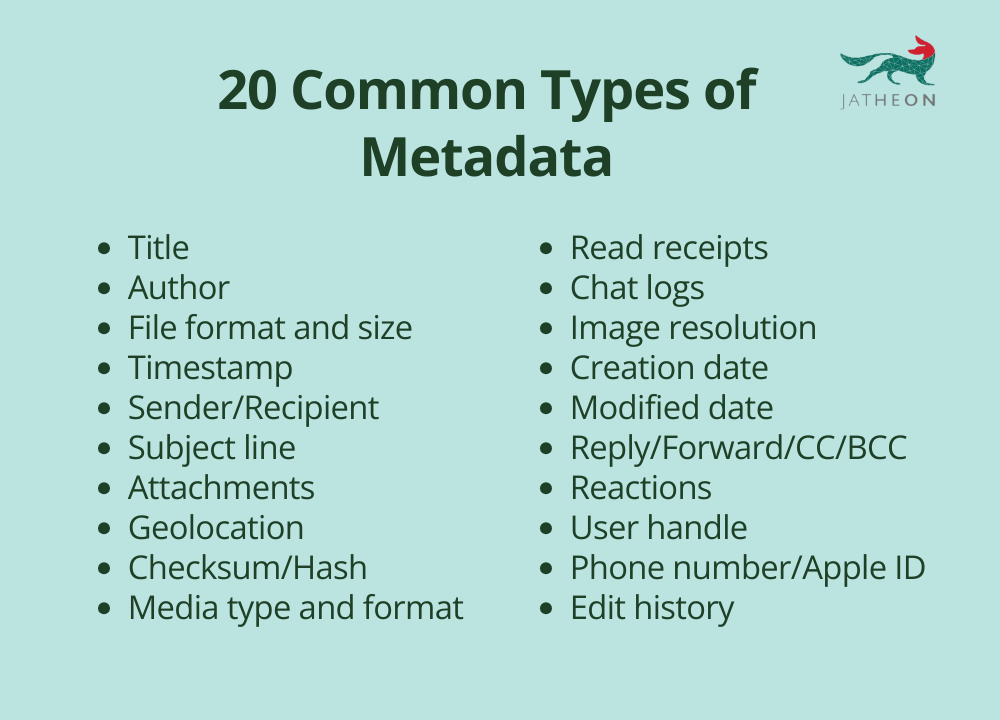
If you’re only here for a quick list of types of metadata, here it is:
If you want to explore this topic in more detail, here’s what you’ll find in this article:
- What is metadata, and why it’s important
- Common types of metadata and their functions
- Real-world examples of metadata in documents, emails, and databases
- How metadata is used for compliance, cybersecurity, and digital forensics
- The role of email metadata in IT management and legal cases
- Whether metadata is admissible in court and its impact on investigations
What Is Metadata?
Metadata is structured information that categorizes, explains, and adds context to your data. It provides critical details about files, making it easier to store, retrieve, search, and analyze information.
In data management and archiving, metadata ensures that organizations can efficiently track, locate, and control digital assets while maintaining compliance with regulatory standards.
For example, metadata in an enterprise document management system may include:
- File name and format — Helps classify and organize files for easy retrieval.
- Author and creation date — Tracks document ownership.
- Modification history — Provides a log of changes, ensuring transparency and compliance.
- Access permissions — Specifies who can view, edit, or delete files.
- Retention policies — Defines how long a document must be stored to meet legal requirements.
- Sender, recipient, timestamps, and IP addresses — Essential for compliance with regulations like FINRA, HIPAA, and FOIA.
By maintaining structured metadata, IT administrators can streamline records management, reduce storage costs, and support legal discovery requests without searching through massive amounts of raw data.
Nearly all digital information contains metadata, including:
- Documents — Microsoft Word files, PDFs, spreadsheets, and presentations store metadata like author, creation date, modification history, and file size.
- Messages, calls, and online communication — Texts, phone calls, emails, social media, chat apps (e.g., WhatsApp, Slack), and video conferencing platforms (e.g., Zoom, Microsoft Teams) generate metadata such as sender/recipient details, timestamps, device info, IP addresses, attachment details, and message status, essential for compliance, security, and legal discovery.
- Images and videos — Digital media files contain technical metadata like resolution, format, compression settings, and GPS location (in the case of geotagged photos).
- Databases — Structured databases use metadata to define table relationships, field types, indexing, and access permissions.
Webpages — Websites rely on metadata elements such as meta titles, descriptions, and keywords to improve search engine visibility (SEO). - Enterprise cloud storage — Cloud-based platforms, like Google Drive or Microsoft SharePoint, attach metadata to files for version control, access logs, and retention policies.
Common Metadata Types
Understanding metadata types is crucial for building effective data governance frameworks. It can be classified into several categories based on its function and purpose.
Each type contributes to data retrieval, compliance, and long-term archiving, ensuring that organizations maintain structured and accessible records.
- Descriptive metadata — Helps users search, categorize, and identify files quickly, commonly used in document management and email archiving. Examples include title, author, keywords, subject, summary, file type.
- Structural metadata — Defines how different components relate within a dataset or document, ensuring proper organization and retrieval. Relevant examples are Table relationships, document hierarchy, email threading.
- Administrative metadata — Controls file security, access, and retention policies, ensuring compliance and governance. Some examples are access permissions, copyright details, security classifications.
- Technical metadata — Describes format, encoding, and compression settings, helping with storage, data migration, and digital forensics. Examples include file size, encoding type, compression settings, bit depth.
- Provenance metadata — Tracks document history, modifications, and previous versions, essential for ediscovery and compliance audits. Examples are edit timestamps, version history, user activity logs.
Nearly all digital files contain metadata, whether in documents, emails, images, databases, or cloud storage systems. Understanding and managing metadata effectively helps organizations improve searchability, maintain compliance, and enhance security.
The Role of Metadata in Data Management and Compliance
Metadata is a dynamic tool that helps organizations to unlock the full potential of their information assets through facilitating efficient retrieval, robust security, and streamlined compliance processes.
Data organization and retrieval
One of metadata’s primary functions is improving how digital information is stored and accessed. Without it, organizations would be left with an overwhelming amount of unstructured data, making it difficult to locate specific files, emails, or records.
- Enterprise file storage — Metadata categorizes files using attributes like titles, keywords, and creation dates, allowing employees to retrieve documents with minimal effort.
- Email archiving — IT teams use metadata to create searchable archives where emails can be retrieved based on sender, recipient, subject, or date.
- Database management — Metadata defines relationships between tables and fields, ensuring that structured data remains properly indexed and easily retrievable.
A well-organized metadata framework significantly reduces downtime, improves search accuracy, and enhances collaboration across teams.
Regulatory compliance and legal requirements
Regulated industries such as healthcare, finance, and government must maintain metadata to comply with various laws and standards. Metadata helps track document history, verify authenticity, and enforce mandatory retention periods.
Several laws and regulations mandate metadata retention and proper management:
- HIPAA (Healthcare compliance) — Medical institutions must store metadata about electronic health records (EHRs) to ensure access logs are maintained and privacy regulations are met.
- FINRA (Financial industry regulation) — Banks and investment firms archive email metadata, including timestamps and sender/recipient details, for fraud investigations, insider trading, and audits.
- FOIA (Public records requests) — Government agencies retain metadata on emails, documents, and other records to comply with Freedom of Information Act requests.
- FISMA (Federal Information Security Management Act) – Demands federal agencies to maintain metadata logs for cybersecurity audits, access tracking, and incident response.
- GDPR (General Data Protection Regulation) — This regulation refers to the EU but affects U.S. businesses handling EU data, and it Requires organizations to protect, limit, and provide access to metadata that contains personally identifiable information (PII), including IP addresses, geolocation, and user logs.
- FERPA (Family Educational Rights and Privacy Act) — Requires schools to protect metadata in student records, including access logs, email metadata, learning management system activity, and document history, ensuring privacy, audit trails, and compliance with retention policies.
Without metadata, organizations may face regulatory compliance violations, legal penalties, and loss of critical records required for audits or investigations.
Ediscovery and legal investigations
In legal cases, metadata is often the key to proving document authenticity, establishing timelines, and reconstructing digital events. Courts, law enforcement agencies, and forensic investigators use metadata to analyze digital evidence.
- Email and other digital communication investigations — Metadata reveals crucial details such as when an email/message was sent, who received it, and whether it was modified after being sent.
- Document forensics — Provenance metadata tracks who created, edited, or deleted files, helping attorneys verify document authenticity in litigation.
- Chain of custody verification — Legal teams rely on metadata logs to confirm that digital evidence has remained untampered throughout an investigation.
Organizations that fail to preserve metadata risk losing key evidence or having digital records challenged in court.
One of the most significant cases where metadata played a crucial role was the Enron scandal in the early 2000s. The case involved massive corporate fraud, accounting manipulations, and financial misstatements by Enron executives, leading to the company’s collapse and billions in investor losses.
- Email metadata helped investigators uncover internal communications showing that executives knew about the financial deception but continued misleading investors.
- Document version history metadata revealed that financial reports had been altered, proving deliberate accounting fraud.
- Access logs and audit trails showed who had edited or deleted files, linking specific individuals to the cover-up.
The metadata evidence was used to prosecute Enron’s top executives, including CEO Jeffrey Skilling and Chairman Ken Lay, leading to convictions for fraud, conspiracy, and insider trading. The case also resulted in new corporate regulations, such as the Sarbanes-Oxley Act (SOX), which mandates strict metadata retention for financial and email records.
Cybersecurity and metadata forensics
With metadata, IT teams are able to detect unauthorized access, track user activity, and analyze digital footprints in the event of a security breach.
- User access logs — Metadata records who accessed a document, when, and from which device, helping IT teams detect insider threats.
- Data tampering detection — Forensic investigators analyze metadata to determine whether files have been altered, deleted, or moved.
- Incident response and threat analysis — Security teams use metadata to reconstruct cyberattacks, tracing the source of malicious activity and identifying vulnerabilities.
In cybersecurity, metadata is an essential tool for preventing data breaches, monitoring suspicious activity, and maintaining a secure digital environment.
How Jatheon Can Help
Managing metadata can be challenging without a centralized solution for capturing, storing, and retrieving records. Jatheon’s enterprise-grade archiving solutions ensure secure, long-term retention of emails, files, and digital communications while preserving metadata for compliance audits, litigation, and investigations.
With comprehensive data indexing and advanced search with 40+ search criteria, Jatheon enables IT and compliance teams to automatically capture and store metadata for easy search, compliance and ediscovery. The metadata-based search helps organizations quickly locate records, reducing time spent on audits and investigations.
Beyond compliance, Jatheon enhances security by maintaining access logs and audit trails, preventing unauthorized data manipulation, and ensuring data integrity. It also helps organizations reduce storage costs by identifying redundant records and optimizing data retention.
Summary of the Main Points
- Metadata is “data about data”. It gives information about a file, document, or piece of content, like its author, date and time created, file size, who accessed it or if any edits were made.
- Almost every digital file, such as a document, email, database, image, or video, stores this information.
- Metadata is essential for organizing, securing, and managing digital files. It records key details about file creation, history, and access. This makes it crucial for authentication and compliance.
- Laws like HIPAA, FINRA, FOIA, FISMA, GDPR, and FERPA require organizations to retain metadata for audits, investigations, and legal transparency.
- In ediscovery and legal cases, these elements help verify authenticity, track modifications, and reconstruct digital events, ensuring evidence remains admissible in court.
- Cybersecurity teams use metadata for forensic investigations. Access logs, timestamps, and modification history help detect insider threats, prevent tampering, and analyze cyberattacks.
- When data is archived, key details like file name, creation date, author, document type, and keywords are extracted as metadata.
- Archiving solutions use metadata as search criteria. When a user searches using specific criteria (e.g., “emails from John Doe in December 2023”), the system checks the index for matches in metadata fields, and is able to quickly retrieve relevant files instead of scanning every item separately.
FAQ
Is metadata admissible in court?
Yes, metadata is admissible in court and often used as digital evidence. It helps verify document authenticity, track modifications, and establish timelines, making it crucial for ediscovery, fraud investigations, and forensic analysis.
Can metadata be manipulated or deleted?
Yes, but altering or deleting metadata can compromise data integrity and may be considered evidence tampering in legal cases. Organizations use secure archiving solutions to preserve metadata in a tamper-proof (WORM) format for compliance and investigations.
Why is metadata important for ediscovery?
Metadata provides crucial details about digital evidence, such as timestamps, authorship, and modification history. This helps legal teams authenticate documents, track edits, and establish timelines during litigation.
Is metadata automatically generated?
Yes, metadata is automatically generated whenever a digital file is created, modified, or transmitted. Operating systems, software applications, and digital devices embed details like timestamps, authorship, and access history without user intervention. However, some metadata, such as document tags or descriptions, can be manually added or edited.
Read Next:Comprehensive Indexing – Why It Matters in Email Archiving [Infographic] |