Digital information has become a cornerstone of legal and compliance processes, and it’s crucial to effectively manage digital evidence in case you need to deliver it to court, lawyers, or HR.
In this article, we’ll cover:
- The types of digital evidence
- What the federal rules say about digital evidence
- Real-world digital evidence examples from recent cases
- Tips for effective digital evidence management
In case you’re here just for a quick summary:
- Digital evidence is any information stored or transmitted in a digital format that can be used in court and legal proceedings.
- The most common types of digital evidence are communications data, transactional data, cloud storage data, social media content, and web browsing data.
- Federal Rules of Civil Procedure indicate that parties must provide proof of data integrity and authenticity as evidence.
- Federal Rules of Digital Evidence specify that, for digital evidence to be admissible in court, relevance, authenticity, and integrity need to be proven.
- Digital evidence is the most common in criminal cases like cybercrimes and identity theft, but also in family and employment law, IP protection cases, and proving compliance in regulated sectors.
- Data archiving helps organizations to take a more proactive approach to lawsuit management.
Digital evidence can be found on computers, hard drives, mobile phones, on the cloud, in apps, and any device that stores electronic information.
At its core, digital evidence is about presenting the digital footprint of electronic crimes such as fraud, data breaches, and unauthorized sharing of information.
Whether it’s about ensuring compliance with industry regulations like HIPAA, SOX, or FINRA, digital evidence plays a key role in a legal context.
Types of Digital Evidence
Digital evidence varies depending on the technology and channel used to produce and transmit it encompassing a wide range of formats.
Understanding the different digital evidence types is crucial for IT professionals, legal and HR teams, and compliance roles.
The most common types of digital evidence can be grouped into five categories:
- Communications data — Includes email, text messages, social media posts, conversations on chat apps like WhatsApp, video, audio calls and transcripts on Zoom, or MS Team, or Slack messages. These electronic records can reveal timelines and context that legal cases investigators can use to detect responsible people and actions.
- Transactional data — Encompases records of online transactions, financial records, and logs of online activities. These can be crucial for financial industry fraud and theft, especially to regulatory bodies like FINRA and the SEC.
- Cloud storage data — As more companies migrate to the cloud, data stored on these platforms has become a significant type of digital evidence. This data includes business documents, presentations, and spreadsheets stored on Google Drive or OneDrive. Important files and data can also be stored in cloud-based project management apps, CRM, or emailing tools.
- Social media content — Social media platforms are legitimate sources of digital evidence. Evidence of employee misconduct can reside in posts, comments, messages, and like patterns.
- Web browser history — Browsing history and website visits are crucial in investigating someone’s intentions and timeline of events. It’s exceptionally important in cases involving cybercrimes, harassment, or unauthorized access to company data.
Each digital evidence type has its specific use case as well as method of collection, verification, and analysis.
Their relevance varies depending on the context of the investigation or compliance requirement, however, keeping them all in mind is the best course of action for any organization.
Understand the Federal Rules of Digital Evidence
Is digital evidence admissible in court and under which conditions?
Most state rules about digital evidence are based on the Federal Rules of Civil Procedure, particularly rules 16, 26, 33, 34, 37, and 45, which outline the requirements and guidelines for managing digital evidence in legal proceedings.
Rule 26 is important because it states that parties must disclose electronically stored information that the disclosing party may use to support its claims or defenses.
On the other hand, Federal Rules of Evidence specify that digital evidence is admissible in court under certain conditions that primarily focus on its relevance, authenticity, and integrity.
As for authenticity, this means that the hash value needs to be checked for evidence to be considered viable.
Regarding integrity, it involves demonstrating that evidence has not been altered or tampered with. This is done through maintaining a chain of custody, using cryptographic hash functions, and employing digital signatures are critical.
The use of audit trails or logs that record how electronic data was handled from the point of creation to its presentation in court can also support claims of integrity.
What does this mean for your data?
It means that all the data you capture and retain for compliance and ediscovery must:
- Be the original source code of messages, webpages, and search history.
- Be collected with all the necessary metadata (date sent or created, date received, sender addresses)
- Digital signatures and timestamps must be placed on the retained data to prove its integrity.
- Data must be stored in a WORM format.
- Data should be prepared in EDRM-XML format for easy processing.
In short, the data must be both in its original format and valid to the case at hand.
Real-World Digital Evidence Examples and Their Impact
Let’s go from theory to practice and look at recent cases where digital evidence had huge implications in real cases.
Mackey v. Belden, Inc.
In the 2021 case of Mackey vs. Belden, case highlighted the importance of data breaches.
Plaintiff was a Belden employee, who, while employed, received a letter stating that her PII (social security number and bank account information) may have been exposed in a data breach. Several weeks later, Plaintiff was notified that unauthorized individuals attempted to file a tax return on her behalf using her social security number.
The court found that the theft of social security numbers, followed by the filing of false tax returns was sufficient to confer standing. This connection between a data breach and subsequent harm established proved as a valid legal crime.
In this case, the digital evidence was more direct as the evidence itself was the instance of a data breach being the cause of harm done.
Zimmerman vs. Weis Markets, Inc.
In the case of a man named Zimmerman vs. Weis Markets, social media evidence was used to prove a false case.
Zimmerman, who suffered an injury while operating a forklift at Weis Markets, claimed he lost wages and endured emotional trauma that prevented him from wearing shorts in public, demanding a payout from the company.
However, the defense found evidence on Zimmermn’s public social media profile contradicting this claim, including photos of him riding a bicycle while wearing shorts.
This evidence was enough to let the court demand Zimmerman’s social media login credentials, proving his false claims.
Waymo vs. Uber
In a 2018 case where Waymo, a self-driving car company, sued Uber for theft of trade secrets, email was used as evidence.
The case centered around email conversations and other documents indicating that the former Google engineer who worked for Uber allegedly downloaded confidential files related to Waymo’s technology.
The emails found played a significant role in the case, demonstrating how digital communication can be crucial evidence in intellectual property litigation.
Effective Digital Evidence Management Through Archiving
The key to proper digital evidence management is how you capture and keep your data organized.
Data archiving can’t be selective if you’re going to comply with major data retention laws.
Everything needs to be archived, with no exceptions, as you can never know which data can be considered evidence.
Cloud archiving solutions like Jatheon capture all data at the point of its creation or when it’s received, from all different communications channels: email, social media, text messages, Zoom calls, MS Teams chat, WhatsApp and others.
The data is all stored in one place, giving you easy access to everything, without the need for multiple archiving solutions.
Once captured, the data is indexed and written in a WORM format. This means that when called upon, you can compare the data in your archive and its value in the index, proving its integrity and making it viable evidence.
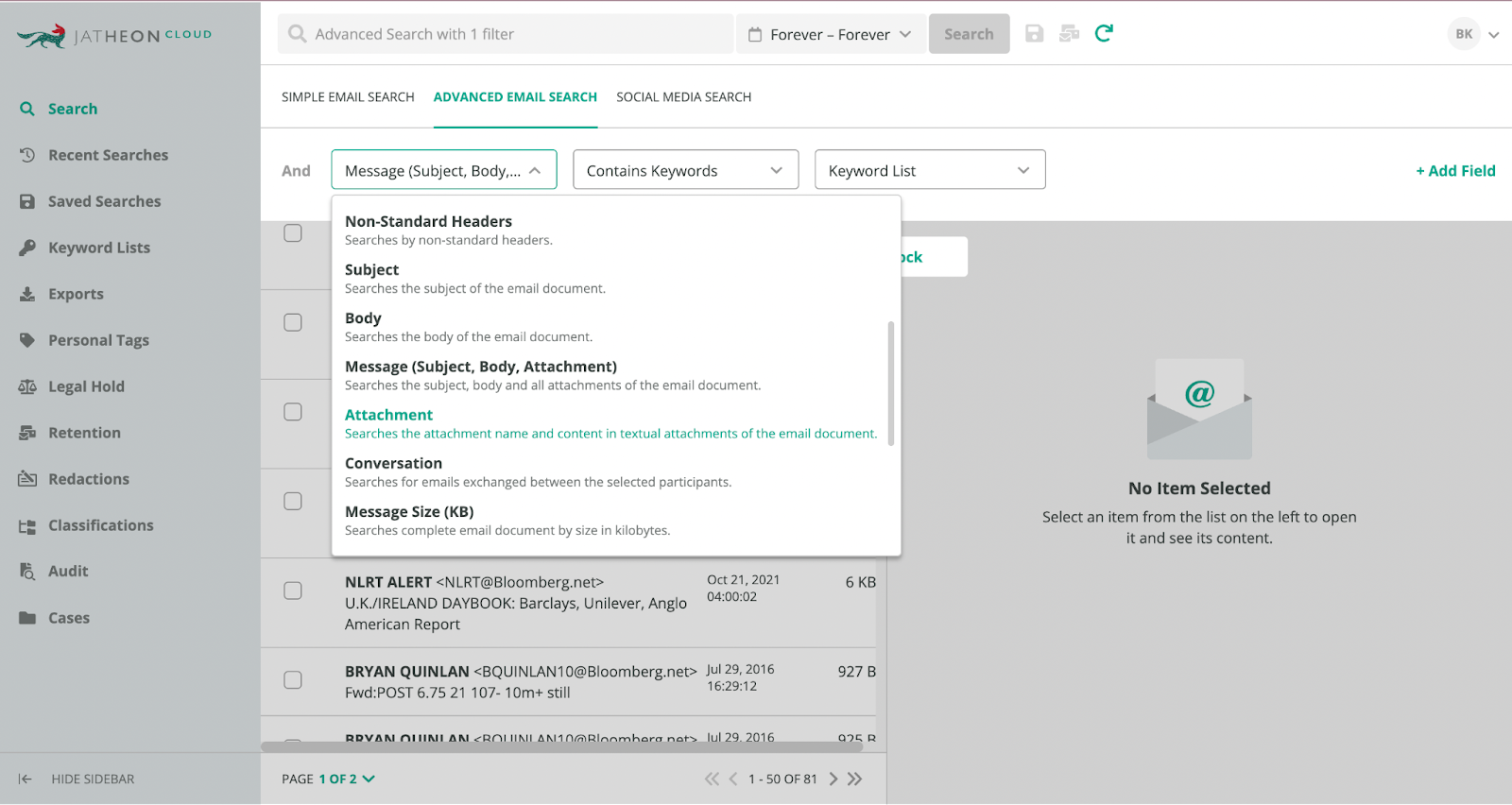
The archived data is easy to find thanks to advanced filters like keyword, fuzzy, boolean, and proximity operators that you can use to perform evidence ediscovery.
Once found, digital evidence can be placed on a legal hold and stored in a separate “evidence” folder allowing for easy digital evidence management.
All in all, data archiving solutions make your compliance job much easier. What’s more important, they help you take a proactive approach to lawsuit management.
Stay compliant with major data retention laws with Jatheon’s cloud archiving solution. Capture data automatically, find important information, and manage your data with ease.
Read Next:Why Email Archiving Is Crucial for Email Ediscovery |