At work and in our private lives, we use SaaS products and apps that use our data.
Think Google Workspace, LinkedIn, Zoom, Slack, Salesforce, HubSpot, Netflix, and Instagram, to name just the biggest ones.
To guard themselves against data breaches (and massive fines that follow breaches) and reputation damage, SaaS companies need to meet SOC 2 compliance — a set of measures to show that they have established information security controls, procedures, and policies.
In this article, we’ll cover:
- What is SOC 2.
- What are SOC 2 compliance and audits.
- SOC 2 compliance checklist.
- The benefits of having a SOC 2 certification.
- How to overcome SOC 2 challenges.
What Is SOC 2?
SOC 2 (Systems and Organization Controls 2) controls how companies store customer information in the cloud.
It was developed by The American Institute of Certified Public Accountants (AICPA) as a security framework that helps organizations show their commitment to data security by specifying how they should protect customer data from unauthorized access and security incidents.
SOC 2 focuses on five controls or trust services criteria (TSC):
- Security — The systems and information are protected against any damage, unauthorized access, and unauthorized disclosure of information.
- Availability — The systems and data are available for use.
- Integrity — The data is processed completely and accurately.
- Privacy — Any personal information is collected, utilized, kept, disclosed, and removed accordingly.
- Confidentiality — All information classified as confidential is protected accordingly.
SOC 2 compliance is split into two distinct reports:
- Type I describes an organization’s systems and whether their design complies with relevant trust principles. It evaluates a company’s cybersecurity program at a certain point in time, looks at how it’s designed and does not require evidence.
- Type II details the operational efficiency of those systems. It evaluates a company’s cybersecurity program over a longer period (6 months to a year), looks at how the program is executed and requires evidence.
Achieving SOC 2 compliance requires a thorough assessment of an organization’s internal controls and processes, and is often conducted by independent auditors.
What Is SOC 2 Compliance?
SOC 2 compliance refers to the SOC 2 framework itself, as well as the audit check that confirms an organization complies with SOC 2 standards.
This involves implementing and maintaining the necessary controls and procedures to ensure the security, availability, processing integrity, confidentiality, and privacy of customer data.
To get SOC 2-certified, companies need to design a compliant security program and pass an audit by an AICPA-certified certified public accountant.
The auditor’s job is to provide an estimate of how much a company’s cybersecurity policies and procedures are in line with the SOC 2 standard and then provide a report with findings.
To obtain the SOC 2 attestation, a company should meet all the requirements. However, only the Security criterion is mandatory.
The same goes for the company’s subsidiaries, segments, third-party vendors, or software partners (e.g. software resellers, hosted data centers) that manage, process, or store customer data.
Despite being voluntary, the SOC 2 attestation can be used to gain an advantage in the sales process, especially when working with enterprise-level companies, which often refuse to do business with cloud companies that do not possess the SOC 2 certificate.
What Is a SOC 2 Audit?
The SOC 2 audit is usually performed annually by an independent auditor to verify if the company’s controls satisfy the SOC 2 requirements.
Unlike most regulations, it’s not the authority or the regulatory body that prescribes the necessary controls — the company itself defines them and attempts to comply with the trust service criteria (TSC) upon which they are audited.
After the audit, the company is issued a SOC 2 report that can have four results:
- Unqualified — The best outcome, indicating that the company’s controls meet the criteria of SOC 2.
- Qualified — Indicates that there are some issues or deficiencies in the organization’s controls that need to be addressed.
- Adverse — Indicates that the company’s controls do not meet the criteria of SOC 2.
- Disclaimer of Opinion — The auditor wasn’t able to form an opinion on the company’s controls due to limitations in the scope of the audit.
SOC 2 Compliance Checklist
Use the following SOC 2 compliance checklist to prepare your company for an audit and secure yourself a SOC 2 certification:
- Choose your objectives — Specify why you need a SOC 2 report, how important it is for your company, and what benefits are you getting from the SOC 2 certification.
- Define the scope — Outline the systems, processes, and services that will get targeted by the SOC 2 audit by selecting the TSC that applies to your organization based on the type of data you are working with.
- Select the primary TSC — Out of the five trust service criteria, select the one that you need to focus on the most while also covering the other four.
- Conduct internal risk assessment — Identify risks associated with growth, location, or data, and document the scope of those risks from identified threats and vulnerabilities.
- Implement controls — Implement controls to ensure compliance with the selected trust service criteria. These controls should be designed to mitigate risks related to data security, availability, processing integrity, confidentiality, and privacy.
- Develop internal policies — Implement policies and procedures that address each of the selected trust service criteria.
- Assess your readiness — Hire independent auditors to see if you meet the necessary SOC requirements to undergo the full audit.
- Apply for an audit — Authorize an independent SOC 2 auditor to complete your audit checklist and generate a report.
- Establish monitoring — SOC 2 requires constant work on securing your privacy and annual audits requiring you to monitor changes and improve your processes.
It’s important to understand that there’s no one strategy to rule them all. Every organization is different and your SOC 2 compliance checklist might look radically different from another’s.
What Are the Benefits of the SOC 2 Certification?
After passing a SOC 2 audit, your business will be SOC 2 certified, which brings a number of benefits:
- Better information security practices — Once established, the SOC 2 requirements help you streamline your information security standards, improve cyber-attack readiness, and prevent data breaches.
- Competitive advantage — As we mentioned before, customers nowadays prefer to partner with companies with rock-solid information security controls over sensitive, protected, or personally identifiable information handled responsibly.
- Lower data breach cost — Both the service provider and the customer company will reduce costs that go with data breaches, including disaster recovery, technical and legal investigations, damage to reputation, or even loss of business for smaller companies.
- Better monitoring — A vendor with SOC 2 compliance certification proves that they have excellent oversight across the organization and systems. This also means that the software itself is continuously monitored for unusual activity, changes, user access, etc.
- Compliance with other laws — Both the organization and the product will need to meet various other compliance standards. Some examples are HIPAA, FINRA, and GDPR. While having the SOC 2 compliance certification won’t automatically mean that you meet all the requirements of other laws, it’s a great first step that demonstrates that you take information privacy and security seriously.
- Trust — If you can demonstrate that you have all the tools, programs, and controls to anticipate threats, and prevent data from being compromised, you’ll win the trust of your customers, get better reviews, and expand your operations more easily.
- Learn from your mistakes — Once you pass a SOC 2 audit, you’ll have a much better idea of where you stand risk and compliance-wise. Your compliance, legal, and IT teams will get actionable information about potential risks that need working on.
Being SOC 2 compliant is a great investment for any business, especially the ones operating in regulated industries.
Overcoming SOC 2 Challenges
As mentioned, out of the five SOC 2 requirements, you need to have them all in check to pass the audit and prove customer data is safe with you.
However, this is easier said than done.
Customer data needs to be preserved and secured from any unauthorized access or breaches. This means all customer data, from all channels.
Furthermore, the customer needs to be assured of this safety.
Modern technology has come a long way in protecting private information, and data archiving is one of the ways you can protect customer data.
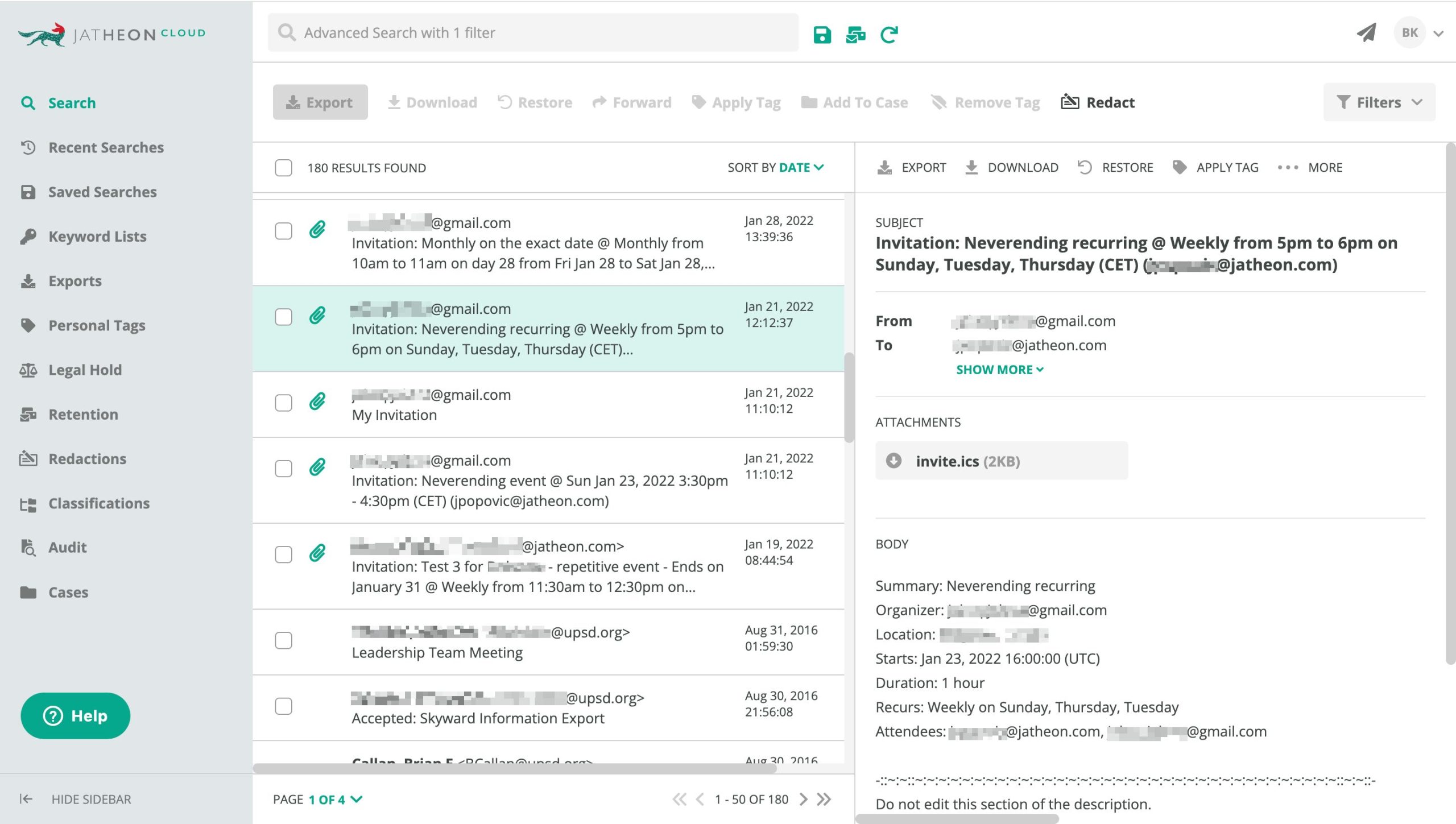
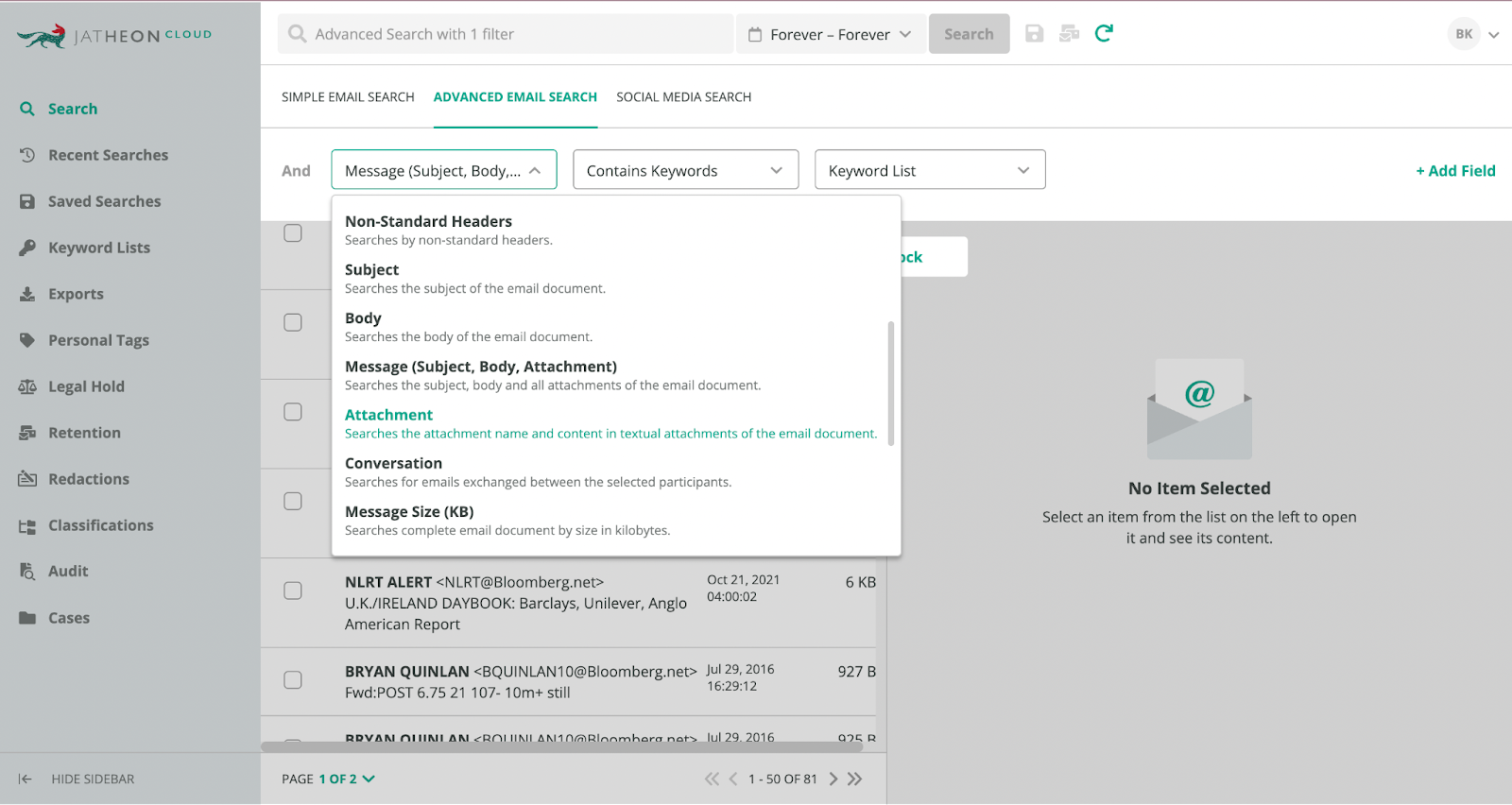
Archiving solutions like Jatheon help you capture all communications data from different sources like email, social media, WhatsApp, Zoom, Teams, or text messages.
This data is protected by industry standards encryption protocols, two-factor authentication, geofencing, and advanced user role and permission settings that allow your IT admins to prevent unauthorized personnel from accessing this data.
However, when needed by the availability SOC 2 requirements, this data can easily be retrieved by utilizing powerful search operators.
Along with SOC 2 compliance, implementing an archiving solution is a surefire way to make your organization compliant with almost all major data protection laws and regulations.
Conclusion
Let’s quickly go over the most important points:
- Customer trust is the key to more business in a dangerous digital environment.
- SOC 2 controls how your business stores customer data and focuses on five controls: Security, Availability, Integrity, Privacy, and Confidentiality.
- SOC 2 compliance is achieved by passing an audit performed by an independent auditor.
- To secure SOC 2 compliance you need to implement specific controls, develop internal data policies, and assess your readiness before applying for an audit.
- Passing a SOC 2 audit means you are trusted in the way you handle data, you comply with other major laws and regulations, and you have strong enough measures to fend off breaches and unauthorized access.
- Utilizing data archiving software secures customer data for long periods helping you comply with SOC 2.
Stay compliant with major data retention laws with Jatheon’s cloud email archiving solution. Capture data automatically, find important information, and manage your data with ease.
Stay compliant with major data retention laws with Jatheon’s cloud email archiving solution. Capture data automatically, find important information, and manage your data with ease.
FAQ
What is the difference between SOC 2 and ISO 27001?
SOC 2 and ISO 27001 are very similar. ISO 27001 requires an IMSM (information security management system), while SOC 2 focuses on security controls. In the U.S., both are accepted, but SOC 2 is preferred. Outside the U.S., ISO 27001 is more common. Both are widely accepted except in healthcare and the federal government.
Who must be SOC 2 compliant?
Any cloud-hosted organization that handles sensitive customer information needs to consider becoming SOC 2 compliant. This includes most software, SaaS, and data companies.
What does a SOC 2 audit include?
The auditor will examine, review, and test your policies, procedures, system configurations, and observe control processes in action. You’ll be asked to provide documentation and evidence. The final document will give an overview of your control landscape and the auditor’s opinion on its effectiveness, plus the recommendations for improvement.
Is SOC 2 mandatory?
SOC 2 isn’t a legal requirement for any organization. However, it may be required by customers, prospects, and other stakeholders looking for assurance that your system has the right controls in place to protect their data.
Read Next:Top 8 Cloud Security Trends To Follow In 2024 Data Retention Policy Explained: A Comprehensive Overview Data Loss Prevention Policy In-Depth Guide and Best Practices |